Google’s Threat Intelligence Group has released its latest report on zero-day exploitation trends for 2024 (download PDF), and while the numbers are down slightly from last year, the data shows we’re still dealing with a highly active and increasingly complex threat landscape.
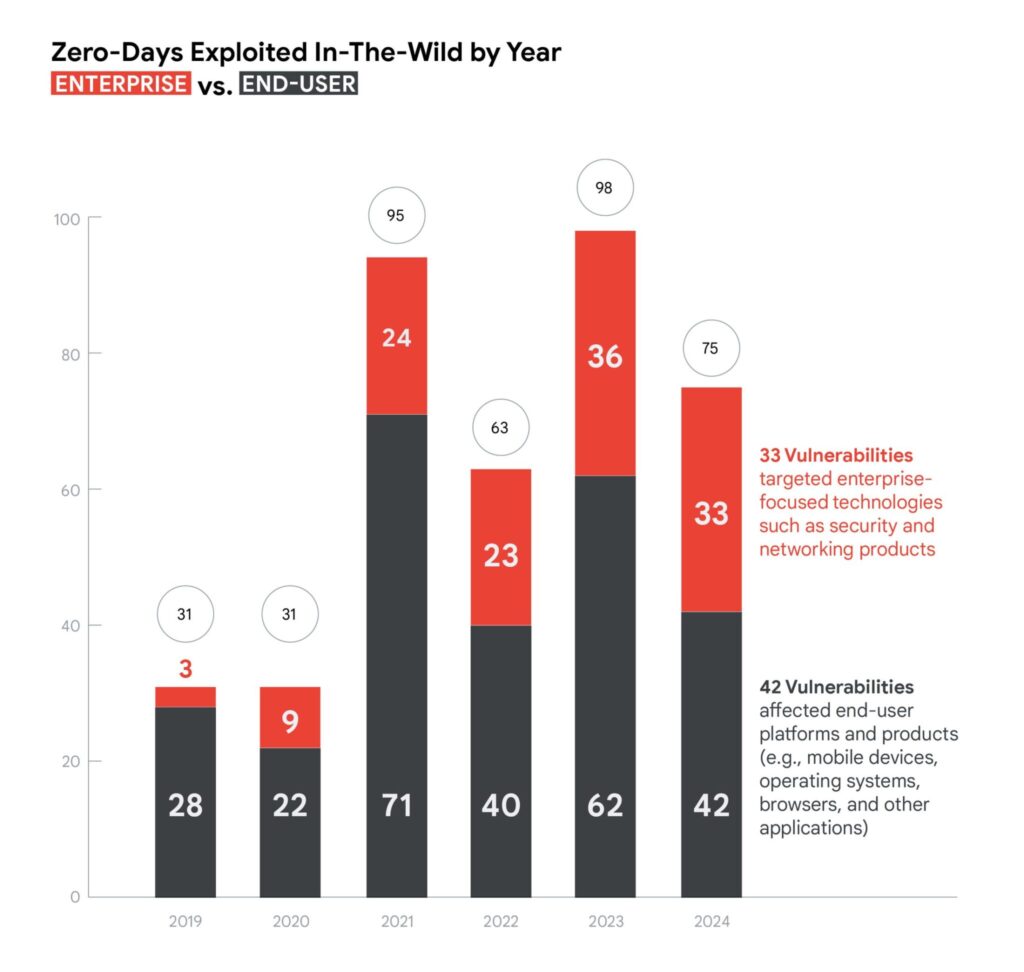
Google tracked 75 zero-day vulnerabilities exploited in the wild before patches were available. That’s down from 98 in 2023, but still well above the 63 recorded in 2022. Of those 75, 33 targeted enterprise technologies like networking and security appliances, while the rest affected end-user products, including browsers, mobile platforms, and operating systems.
Mobile devices were a key target, especially through exploit chains involving multiple vulnerabilities. Google found that 90% of those chained exploits were aimed at mobile platforms, with many Android attacks focusing on third-party components.
On the browser side, Chrome remained the most targeted, which Google attributes to its widespread use. Interestingly, Safari and iOS exploit activity dropped significantly compared to previous years, while Windows saw a notable increase.
Enterprise-focused exploits included Ivanti, Palo Alto Networks, and Cisco appliances. These types of systems are particularly attractive to attackers because:
- Endpoint detection and response (EDR) tools often don’t monitor them effectively.
- Exploit chains aren’t always necessary, as individual vulnerabilities can be enough to achieve remote code execution or privilege escalation.
When it comes to attribution, Google was able to connect 34 of the 75 zero-days to known threat actors. Here’s how that broke down:
- ~45% were linked to state-sponsored groups, often focused on espionage or financially motivated attacks.
- ~25% were tied to commercial surveillance vendors.
- ~30% involved non-state actors, primarily financially motivated cybercriminals.
The report also pointed out that some cybersecurity firms use a broader definition of “zero-day,” sometimes including any newly discovered vulnerability, even if it hasn’t been exploited. Google’s analysis focuses strictly on vulnerabilities actively exploited before a public patch became available.
Overall, while the volume of zero-days dropped slightly, the shift in targeting behavior—especially toward mobile devices and edge enterprise infrastructure—suggests attackers are adapting quickly to new opportunities and gaps in visibility.
Leave a Reply